We live in the era of the data gold rush. Governments tracking your movements, corporations keeping a tab on your digital footprints to give you targeted ads, desktop programs and smartphone apps using clauses in user license agreements to record and sell data like your browsing habits and shopping preferences—no one likes that feeling of constantly being watched. While common forms of private web browsing like using Chrome’s Incognito mode, or Microsoft Edge’s InPrivate mode will prevent others who use the PC or smartphone from going through your browsing history, their degree of “privacy” is limited. You’re not really anonymous, since your ISP can still monitor the sites you visit. The Tor Project comes in for complete anonymity.
Short for “The Onion Router”, Tor has been developed to keep you anonymous while browsing, ensuring that your location and identity are always private, and that there won’t be any tracks of your online activities. This software was initially developed in the 90s by the United States Naval Research Lab to cloak their activities and ensure that they wouldn’t be traced back to them. It uses an onion-like layering technique—hence the name, concealing information on location and user activity. While it has its roots in military use, it is now free and open-source, and used all over the world—from fostering democracy and dissemination of information within authoritarian states, to the average internet Joe simply looking to surf the web without feeling that they are under a microscope. Here is how you can use it:
Installing Tor Browser
- Head on over to Tor Project and download the software version that suits your operating system.
- Run the installer, and once it’s complete click “Finish” to launch it.
- A settings dialog will pop up, with settings to connect to the Tor network. Simply click the “Connect” button. However, if you’re connecting to the internet via proxy, click the “Configure” button and key in the settings.
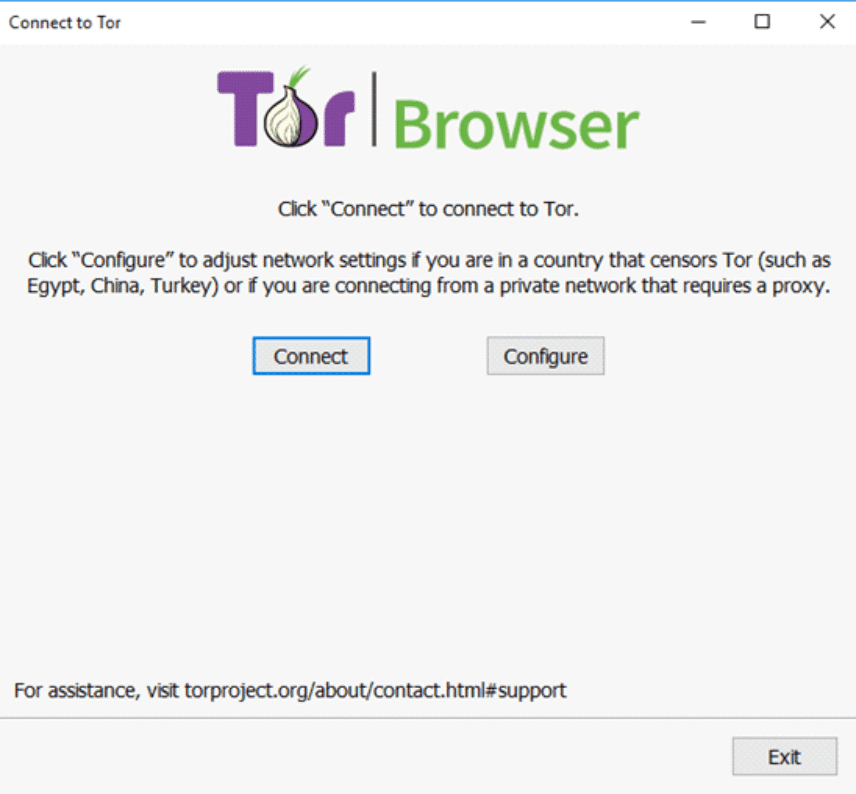
For the initial connection, the program may take several minutes—and it warns of this, since it is making the connection through relays. However, after this is done, the Tor browser launches, ready to be used.
If you’ve surfed with Mozilla Firefox, then you’ll find Tor to be familiar, since they are based on the same code. You don’t have to have used Firefox before to get a hang of Tor though. There are similarities to Chrome, Microsoft Edge and Safari, so you will get used to it really quickly.
Setting the security levels
With the default security settings, they are set to “Standard”. This alone is still far more secure compared to the conventional web browsers. However, you can increase this further, selecting the preferred security level—but keep in mind that some functionalities on the sites you visit will be disrupted.
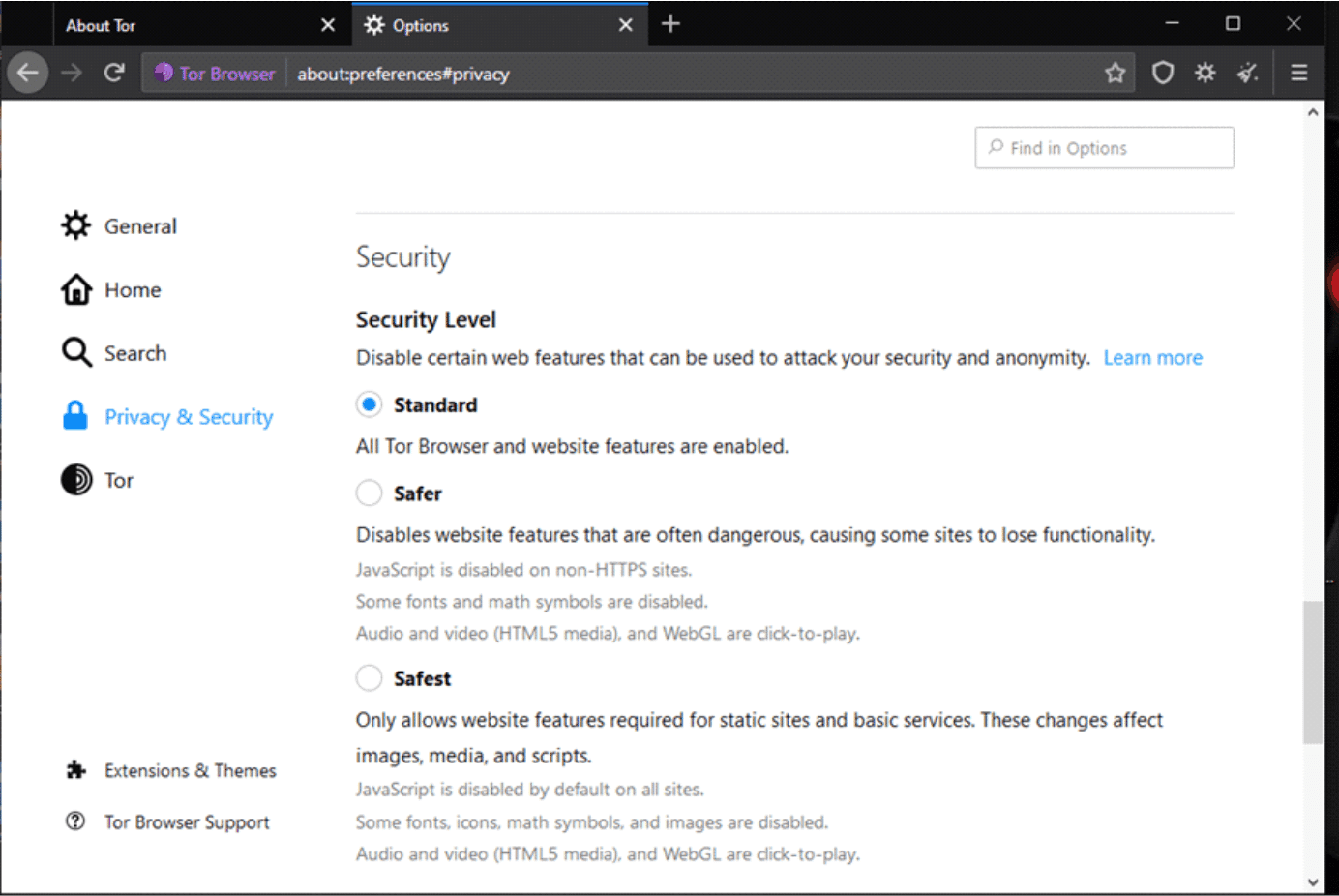
The goal here to achieve a balance between the desired level of privacy, security and web usability.
Understanding How Tor Works
How does Tor work to keep your connection private and anonymous? It avoids direct connection to websites. Instead, the connection gets passed through multiple nodes on the network. These nodes are servers operated by volunteers. As it bounces around the different nodes, these intermediaries won’t know the source of the connection (you) or the target destination (the website you visit). This makes it impossible for the website to determine who you are and track you. For example:
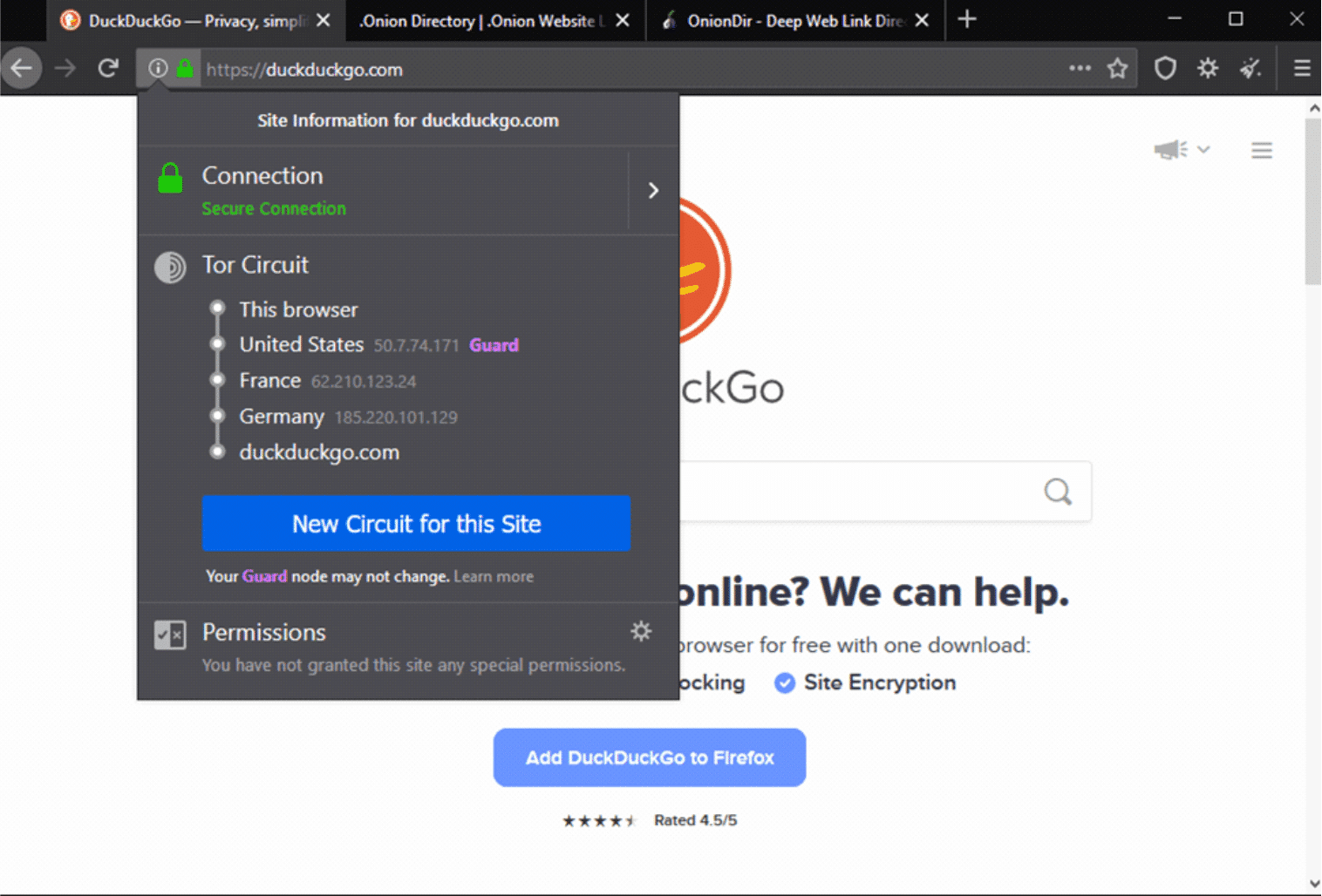
Here’s what happens: The data leaving your computer or smartphone is encrypted, then sent into the Tor network. As it passes each individual node, a layer of encryption gets removed, revealing the location of the next node. When it gets to the last exit node, the final encryption later is removed, for the data to be sent to its destination. The path is randomly generated, the relays do not keep records, and each node just decrypts enough information to know the previous and next node on the path. This mode of operation will be why you’ll notice the slightly lower surfing speed when using Tor compared to other browsers. However, on a good internet connection, the difference in site loading speeds will be minimal.
In case the performance gets unusually slow, or pages become unresponsive, you can launch a new Tor circuit. This option is on the drop-down menu, shown below:
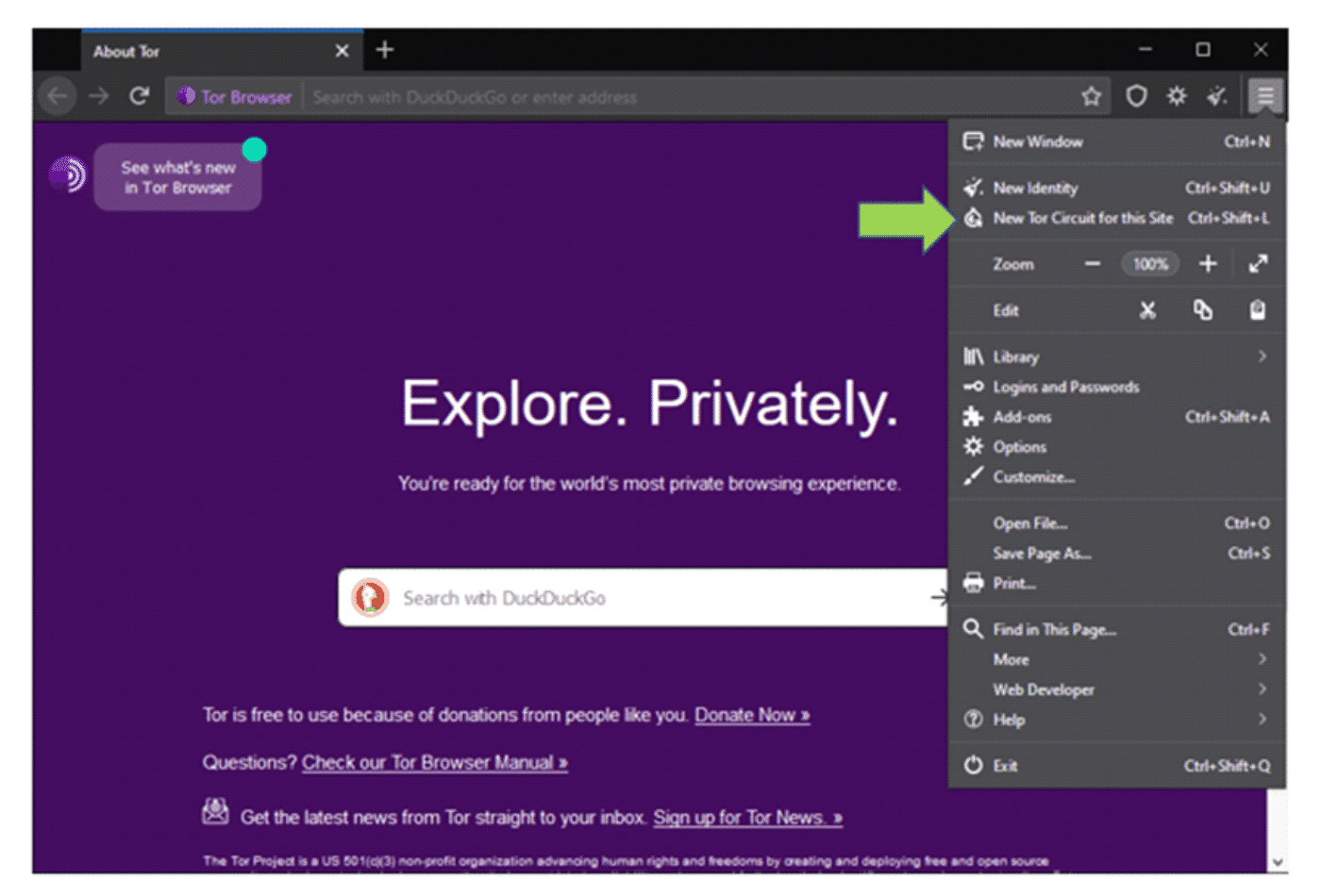
The “New Tor Circuit for this Site” option only applies for that active tab. You may want to go the extra set of acquiring a whole new identity, and that option is also available. Note that selecting this closes and restarts Tor, in order to give you a new IP address and set up a different connection.
Changing your modus operandi
There are some surfing activities that you’re probably used to, which you should change when using Tor browser. These include:
- Using Google or Bing to make your searches online. It’s recommended that you switch to privacy-focused search engines like DuckDuckGo.
- Browser extensions are ill-advised. These can leak out your private information—beating the purpose of using this mode of browsing in the first place. As such, you should avoid installing them.
- As you browse through the different sites, popups may show up, giving you different warnings- especially when there are items on that site that can be potentially used to track you. These popups will depend on the privacy settings you selected, and the sites you visit.
- You should also ensure that you use the HTTPS version of sites, rather than the less secure HTTP. Don’t fret—you don’t have to keep remembering this. Tor Browser by default automatically tries to direct you to the HTTPS version of the site being visited if it is available. Keep your eye on the URL bar just in case.
- If you’re keen on staying anonymous, it is recommended that you turn off the plugins and scripts. This is because, just as is with any other browser, plugins and scripts can be exploited to reveal data like your IP address.
- Torrenting is also discouraged on Tor. The torrent traffic is not protected, and this can be used to reveal your IP address. It will also be slower, given the number of relays that the data is passed through.
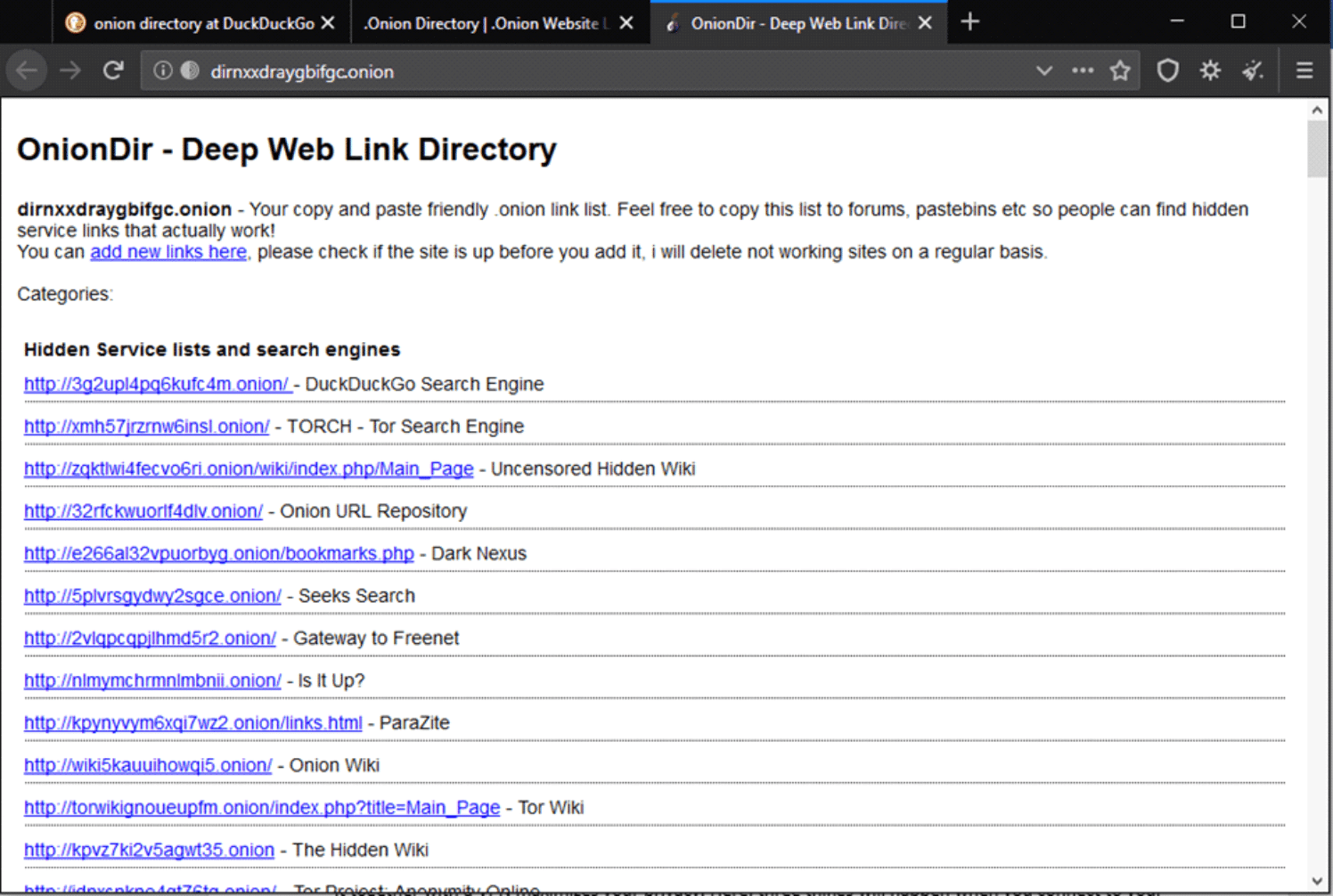
- Visiting .onion sites gives you more privacy. These are the “deep web” or “hidden Tor services”, which can’t actually be accessed by search engines. You’ll need to get the direct links to them. Sounds like a lot of work, right? It’s not like you’re walking around with a list of preferred sites, and you don’t always know the particular onion site which has what you need. Onion directories come in to help you out.
Crank things up a notch with a VPN
Surfing the net with a Tor browser also draws attention to you. While the ISP cannot exactly know what you’re doing, it can still see that you’ve been connected to the Tor network, thus raising suspicion about your activities. Using it together with a VPN maximizes your privacy. Here, three things will happen when you connect to your VPN before launching the Tor browser:
- No Tor relay/node sees your IP address
- The VPN doesn’t see your activity in the Tor browser
- Network operators won’t know you’re using Tor


